A breakthrough that might break the internet

In today’s Finshots, we take a look at how a chip named Willow recently proved that reliable quantum computing is not science fiction anymore, and how this might affect you and me sooner than you think.
But here’s a quick side note before we begin. Trust Finshots for Finance? You’ll love Ditto for insurance.
Built by the same four friends behind Finshots, Ditto is here to make insurance simple. No spam, only honest advice to help people make smart insurance decisions.
✅Backed by Zerodha
✅Rated 4.9 on Google (13,000+ reviews)
✅7 lakh+ customers advised
Click here to talk to an IRDAI-Certified advisor for FREE.
Now on to today’s story.
The Story
It is believed that hackers around the world are quietly intercepting and hoarding vast volumes of encrypted data, including your biometrics and bank account details, to top-secret research by governments and labs. However, they can’t open these files.
At least not today.
But within the next few years, they may have a reliable way to access them. In fact, back in 2020, Sundar Pichai predicted that within 5 to 10 years, quantum computing will break today’s encryption systems. And just last week, Google’s Quantum Computing division made a breakthrough in that direction. It successfully ran a new algorithm named Quantum Echoes on the Willow chip. And this achieved a verifiable ‘quantum advantage’. In simple terms, it ran complex simulations 13,000 times faster than the world’s best supercomputer.
Even better, the results were reproducible and more reliable, which is something previous quantum experiments struggled with. In short, Google just showed that quantum computing is inching from lab theory to real-world potential, a leap that could soon affect everything from chemistry to finance to cybersecurity.
That’s where the real promise of quantum computing lies. Since quantum computers can process so many possibilities simultaneously, they’re uniquely suited for complex simulations and optimisation tasks. For instance, in chemistry and materials science, they could help chemists model molecular interactions precisely to design new drugs, superconductors, or even next-generation batteries. This is something today’s supercomputers struggle to do because the math becomes astronomically complex.
However, this alone doesn’t mean that quantum computers don’t come with downsides. The biggest one being that they can easily break modern encryption standards, and destroy the foundation of digital security. And in order to understand how, let’s first see how it works today.
Encryption for emails or other digital signatures essentially works by multiplying two prime numbers.
Let’s say you log in to a website such as your bank. Your data isn’t sent in plain text. It’s scrambled using a public key, which is a mathematical code made by multiplying two very large prime numbers, often hundreds of digits long.
And here’s where the trick lies. Multiplying them is easy. But if someone tries to do the reverse, i.e., figure out which two primes were multiplied to create that massive number, it’s practically impossible for classical computers. This process is called RSA encryption (and yes, it’s built on that prime-factorisation concept my 5th grade maths teacher taught me).
This ensures that your data remains secure and reliable and that two people who have never met can exchange information safely. One person encrypts the message using a public key, and the other decrypts it with a private key.
To give you an idea of scale, even the most powerful supercomputer today would take billions of years to crack a 2048-bit RSA key by brute force.
That’s why the system is considered secure. Your bank details, passwords, and digital certificates all depend on this principle that breaking down a huge number into its prime components takes an unimaginably long time.
Quantum computers, however, don’t play by the same rules. They use something called ‘superposition’, which allows them to process multiple possibilities at once instead of checking each one sequentially.
To understand this, here’s a famous thought experiment proposed by Erwin Schrödinger, one of the pioneers of quantum physics (you may be familiar with it if you’ve watched the American sitcom, The Big Bang Theory):
A cat is placed inside a sealed box with a small amount of radioactive material that may or may not decay, triggering a mechanism that could release poison. Until someone opens the box, the cat isn’t just alive or dead; it’s both alive and dead at the same time. Its actual state exists as a combination of both possibilities until it’s observed.
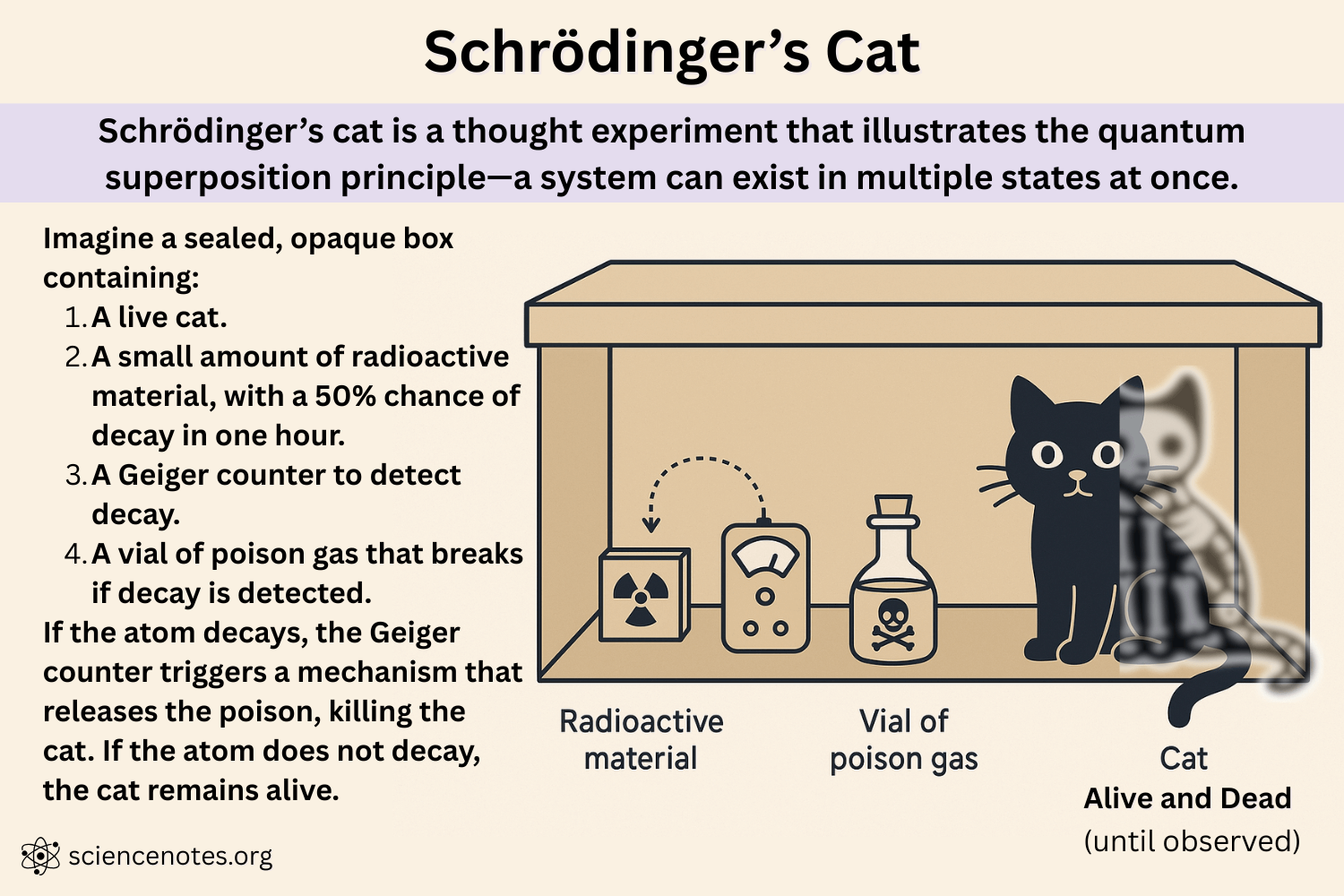
Quantum computers apply the same idea to computing. While classical computers use bits, which can be either 0 or 1, quantum computers use ‘qubits’, which can be 0, 1, or any combination of both simultaneously. This means that a quantum computer can process many possible answers simultaneously, something that no classical computer can do.
And with the help of an algorithm known as Shor’s algorithm, a sufficiently powerful quantum computer could factor large prime numbers exponentially faster, effectively breaking the RSA encryption in hours or days.
And that’s exactly the threat experts are worried about.
It means the same technology that promises breakthroughs in medicine and materials could also render the world’s online banking systems, government communications, and private data completely exposed.
That’s why security agencies and corporations worldwide are now racing to prepare for what they call Q-Day (the day quantum computers become powerful enough to break existing public-key encryption).
Governments, tech companies, and research institutions are already working on solutions such as “quantum proof” systems. The US National Institute of Standards and Technology (NIST) has been running an international competition since 2016 to identify Post-Quantum Cryptography (PQC) algorithms. These are basically new encryption methods that even quantum computers can’t easily crack.
In 2022, NIST announced four leading algorithms: CRYSTALS-Kyber for general encryption, and CRYSTALS-Dilithium, Falcon, and SPHINCS+ for digital signatures. These are designed using complex mathematical problems that even the most advanced quantum computers can’t solve efficiently (for now).
Meanwhile, companies like Cloudflare are testing hybrid encryption systems that combine traditional encryption, like AES, with quantum-resistant algorithms to safeguard future data transfers.
In India, the government launched the National Quantum Mission in 2023 with a ₹6,000 crore investment to strengthen the country’s capabilities in quantum computing, communication, and cryptography.
And that’s where the strange irony lies. The same technology that could help us discover new drugs, design better batteries, and solve humanity’s most endearing problems, which we once thought were impossible to solve, could also expose every secret we’ve ever tried to keep.
Until then…
PS: We used RSA merely as an example. In reality, modern digital infrastructure relies on multiple encryption methods such as AES, RSA, ECC, SHA, ECDSA certificates, etc. Some are more secure than others, but most still remain vulnerable to advances in quantum computing.
PPS: Although we didn’t have the opportunity to cite this paper directly, it was interesting to go through how banks and other financial institutions are preparing for Q-Day.
If this story helped you make sense of Willow and quantum computing, do share it with your friends, family, or even strangers on WhatsApp, LinkedIn, and X.
