Why UK manufacturing couldn’t afford a JLR on crutches

In today’s Finshots, we tell you how JLR’s cyberattack brought its factories and the UK’s manufacturing sector to their knees, and why cybersecurity matters just as much as assembly lines.
But before we begin, if you love keeping up with the buzz in business and finance, make sure to subscribe and join the Finshots club, loved by over 5 lakh readers.
Already a subscriber or reading this on the app? You’re all set. Let's get started with the story!
The Story
What happens when the code building your cars stalls before the engines do?
A multi-million pound breakdown, closed factories, and a workforce with no choice but to stay indoors.
This was the reality that Jaguar Land Rover (JLR) faced when a cyberattack struck in August. For almost a month, its factories lay defunct — not just in the UK, but also in Slovakia, Brazil, and India.
In fact, JLR hasn’t produced a single car since 31st August. But it wasn’t the only company under attack.
The UK has seen a string of cyberattacks this year. Marks & Spencer’s (M&S) website and app were down in April due to a ransomware attack. Shoppers couldn’t make online purchases, and services were restored only recently. Another retail chain, the Co-op, also suffered a similar attack that cost it over £80 million in profits.
But while M&S and the Co-op eventually bounced back, the impact on JLR has been far greater. Every week its factories stayed shut, cost the company £50 million.
So why was JLR hit the hardest?
For that you’ll have to first understand what actually happened.
It started two years ago, when JLR signed a five-year, £800 million deal with TCS to rebuild its tech infrastructure. Since JLR has been owned by Tata since 2008, handing the job to Tata’s IT arm seemed natural. The plan was to modernise JLR’s digital systems, including a massive upgrade to SAP software — the system that controls how car parts move around factories, how suppliers are linked, and even how luxury models are customised for top paying customers. In short, it was the backbone of JLR’s global production.
But the problem was that JLR had connected “everything to everything” — from smart factories to supplier systems. So when hackers (likely groups such as Scattered Spider, Lapsus$, or ShinyHunters) struck its core IT systems, production had to be halted immediately. And unlike older setups, JLR had to shut down almost everything, instead of just isolating the affected parts.
The attack blocked access to critical systems that ran production lines, orders, payments, and even basic communication. Which means that JLR couldn’t build vehicles, place or pay for parts, or even process supplier invoices. For weeks, employees, suppliers, and logistics partners were left in limbo.
So the bottom line was that the IT overhaul meant to make JLR more efficient ended up exposing its biggest weakness.
But why does a cyberattack on just one automaker matter so much to the UK, you ask?
Well, you see, JLR began life in 1922 making motorcycle sidecars in the UK. Fast forward a century, and it has grown into a multinational automaker designing, engineering, and building some of the world’s most recognisable luxury vehicles.
Today, it’s not just another car company, but a pillar of the UK’s auto sector and a big cog in the broader economy. To put things in perspective, in 2024 alone, JLR contributed about £17.9 billion to the UK economy. That’s roughly 0.6% of the country’s GDP. It directly employs around 33,000 people in the UK, with a supply chain that supports another 2 lakh jobs across hundreds of firms, many of them specialised local suppliers. In the West Midlands alone, where JLR’s main plants sit, it makes up nearly 5% of the regional economy.
And it’s not just about the sheer volume of cars it produces — nearly 1,000 vehicles a day at peak, but also exports, high-skilled jobs, and innovation in electric vehicles.
So when JLR’s systems went dark, the ripple effects were brutal. Almost half its suppliers reported financial pain including unpaid invoices, delayed orders, and mounting costs. For many who depended solely on JLR, the shutdown meant layoffs, reduced hours, or even the threat of bankruptcy. Banks became reluctant to offer loans to affected suppliers without personal guarantees or collateral such as their homes, pushing many into liquidity crises.
It got so bad that suppliers appealed for government help. And the UK government had to step in, touring factories and eventually guaranteeing JLR a £1.5 billion loan to keep its supply chain afloat.
What you can’t ignore is that this came at a time when UK manufacturing was already reeling from its worst slump since Covid. September was their worst month, with growth falling to a 4 month low, and energy and manufacturing costs rising. And just when things looked fragile, cyberattacks froze production.
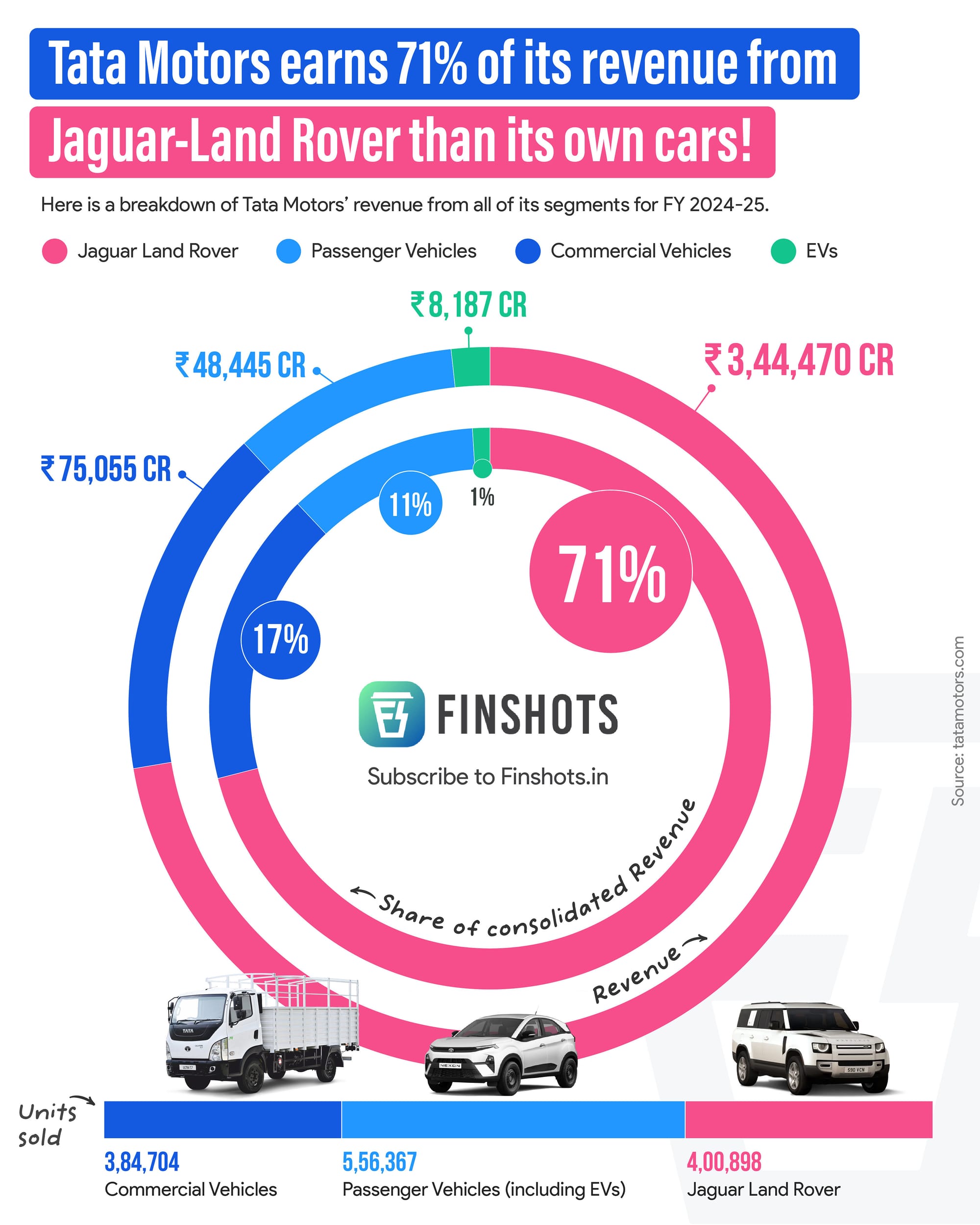
For Tata Motors too, the stakes are high. With 70% of its revenue tied to JLR, the parent company could be staring at a weak profit engine ahead.
And absorbing the hit, especially without the cushion of cyber insurance, only makes the blow harder. Yup, you read that right. A Reuters story suggests that JLR didn’t have cybersecurity insurance, meaning they had to bear all the costs from the attack. They had not finalised a cyber insurance policy brokered by Lockton before the attack and therefore appear to have had no active cover for this incident.
All of this makes you wonder — how do you fix this, and more importantly, stop it from happening again?
It’s going to take more than quick IT fixes. Companies like JLR need to treat cybersecurity the way they treat car safety. It’s not optional. That means building a proper cyber resilience framework that covers both the digital side and the factory floor. Regular risk checks, supplier audits, and learning from past incidents — whether it’s JLR’s own hack or other high-profile breaches, should be the norm.
But the basics matter most. Strong access controls with multi-factor authentication, regular password updates, and systems that can spot unusual activity early can make a huge difference.
On the operational side, JLR needs a “what if everything stops?” plan. Meaning, modern factories need a zero-trust approach where they assume that networks could already be compromised and focus on quick containment and response. Tested plans for downtime, supply chain delays, or production halts are crucial.
And training employees for cyberattacks is just as important as fire drills. They could in fact, simulate attacks before they happen. Tabletop exercises and team drills that mimic real hackers expose weak spots, test defences, and ensure teams know exactly how to respond. Because the faster a company can detect, contain, and recover, the smaller the fallout.
That way the next time a Range Rover rolls off the line, it won’t just be a triumph of engineering, it will be proof that in modern manufacturing, lines of code are as critical as bolts and engines.
Until then…
If this story helped you quickly make sense of the JLR cyberattack and its ripple effects on the UK’s auto industry, share it with friends, family, or even strangers on WhatsApp, LinkedIn, and X. After all, it’s always nicer to have a smarter bunch of folks around you.
Myth Alert: I'm Too Young to Buy Life Insurance!
The other day, one of our founders was chatting with a friend who thought life insurance was something you buy in your 40s. He was shocked that it was still a widely held belief.
Fact: Life Insurance acts as a safety net for your family. The younger you are, the cheaper it is. And the best part? Once you buy it, the premium remains unchanged no matter how old you get.
Unsure where to begin or need help picking the right plan? Book a FREE consultation with Ditto's IRDAI-Certified advisors today.
